ZMap: A Powerful Tool for Network Discovery and Security Auditing
Related Articles: ZMap: A Powerful Tool for Network Discovery and Security Auditing
Introduction
With great pleasure, we will explore the intriguing topic related to ZMap: A Powerful Tool for Network Discovery and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
ZMap: A Powerful Tool for Network Discovery and Security Auditing

ZMap is a high-performance network scanner designed for rapid and efficient discovery of network devices and services. Built with speed and scalability in mind, it leverages the power of modern computing hardware to scan networks at unprecedented rates, making it an invaluable tool for network administrators, security researchers, and anyone interested in understanding the global network landscape.
Understanding ZMap’s Capabilities
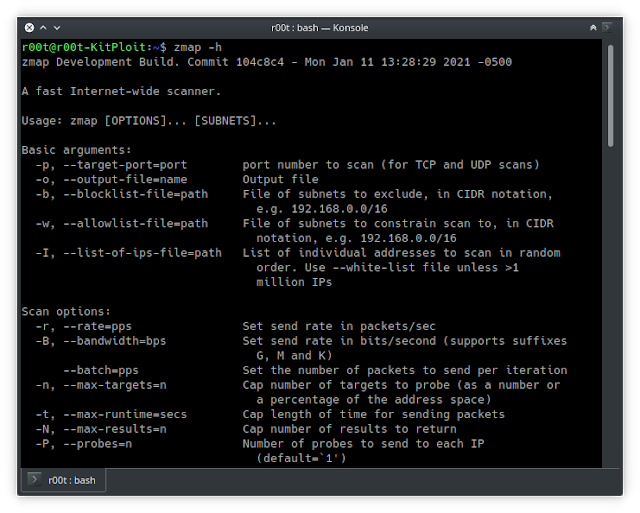
ZMap’s core function revolves around sending probes to a vast number of IP addresses, meticulously analyzing the responses to identify active devices and services. Its design prioritizes efficiency, employing parallel processing and asynchronous I/O techniques to achieve impressive scanning speeds. This allows ZMap to conduct network scans across vast IP address ranges in a fraction of the time compared to traditional scanning methods.
Key Features and Benefits
- High-Speed Scanning: ZMap’s parallel processing capabilities enable it to scan millions of IP addresses per second, significantly reducing the time required for network discovery and security audits.
- Scalability: ZMap can be easily scaled to handle large-scale network scans, making it suitable for probing entire Internet address spaces or specific network segments.
- Flexibility: ZMap offers a wide range of customization options, allowing users to tailor scans to their specific needs. This includes the ability to specify target IP ranges, ports, protocols, and even custom payloads.
- Data Analysis: ZMap provides tools for analyzing the collected data, enabling users to identify network trends, discover vulnerabilities, and gain insights into network behavior.
- Open Source: ZMap is an open-source project, fostering collaboration and encouraging community contributions to its development. This ensures ongoing innovation and improvement of the tool.
Applications of ZMap
ZMap finds diverse applications across various domains:
- Network Discovery: ZMap is used to identify active devices on a network, providing a comprehensive inventory of connected systems.
- Security Auditing: By scanning for specific services and vulnerabilities, ZMap helps organizations identify potential security risks and weaknesses.
- Internet Research: ZMap facilitates research into the global network landscape, enabling researchers to study network trends, service distribution, and protocol usage.
- Botnet Detection: ZMap’s rapid scanning capabilities can be used to detect botnets by identifying large numbers of compromised devices communicating on specific ports.
- Incident Response: ZMap assists in incident response by quickly identifying affected systems and gathering information about the attack.
ZMap in Action: Real-World Use Cases
- Mapping the Internet: ZMap has been used to map the entire Internet, providing a comprehensive understanding of the global network landscape.
- Identifying Vulnerable Services: ZMap has been employed to identify vulnerable services exposed to the Internet, helping organizations prioritize security patching efforts.
- Detecting DDoS Attacks: ZMap can be used to detect DDoS attacks by identifying large numbers of requests originating from compromised devices.
- Analyzing Network Traffic: ZMap can be used to analyze network traffic patterns, providing insights into network usage and identifying potential anomalies.
FAQs
1. What are the prerequisites for using ZMap?
ZMap requires a Linux operating system and a C++ compiler. It is recommended to install the necessary libraries and dependencies as per the official ZMap documentation.
2. How secure is ZMap?
ZMap is designed to be a secure tool, but it is important to use it responsibly and avoid targeting systems without permission. It is essential to follow ethical hacking principles and respect the privacy of individuals and organizations.
3. Can ZMap be used for malicious purposes?
Like any powerful tool, ZMap can be misused for malicious purposes. It is crucial to use ZMap responsibly and ethically, adhering to legal and ethical guidelines.
4. What are the limitations of ZMap?
ZMap’s scanning speed can be affected by factors such as network bandwidth and the responsiveness of target devices. It may also encounter limitations when scanning networks with sophisticated security measures in place.
5. How can I learn more about ZMap?
The official ZMap website and documentation provide comprehensive information about the tool, including installation instructions, usage guides, and examples. The ZMap community forum is also a valuable resource for seeking support and sharing knowledge.
Tips for Effective ZMap Usage
- Start with small scans: Begin with scans targeting smaller IP ranges to gain familiarity with ZMap and its capabilities.
- Use appropriate probes: Select probes that are relevant to your scanning objectives and avoid sending unnecessary traffic.
- Configure logging: Enable logging to track the progress of your scans and analyze the collected data.
- Use filters: Apply filters to refine your scans and focus on specific targets or services.
- Respect privacy: Avoid targeting systems without permission and adhere to ethical hacking principles.
Conclusion
ZMap stands as a powerful and versatile tool for network discovery and security auditing. Its ability to conduct high-speed scans, scale to large networks, and provide valuable data analysis capabilities makes it an indispensable resource for network administrators, security researchers, and anyone seeking to understand the intricate workings of the Internet. By understanding its capabilities and using it responsibly, ZMap can be a valuable asset in securing networks, identifying vulnerabilities, and gaining insights into the global network landscape.



Closure
Thus, we hope this article has provided valuable insights into ZMap: A Powerful Tool for Network Discovery and Security Auditing. We thank you for taking the time to read this article. See you in our next article!