Unveiling Network Secrets: A Comprehensive Guide to Nmap
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling Network Secrets: A Comprehensive Guide to Nmap

Nmap, short for Network Mapper, is a powerful and versatile open-source network scanner. It allows users to discover hosts and services on a network, identify open ports, gather information about the operating system and applications running on those hosts, and much more. This comprehensive guide will delve into the capabilities of Nmap, exploring its core functionalities, advanced techniques, and real-world applications.
Understanding the Essence of Network Scanning
Network scanning forms the bedrock of network security assessment and troubleshooting. It empowers administrators and security professionals to gain visibility into the network landscape, identify potential vulnerabilities, and ensure network integrity. Nmap excels in this domain by providing a robust set of tools and techniques for conducting thorough and insightful scans.
The Power of Nmap: A Glimpse into its Capabilities
Nmap’s capabilities extend far beyond basic port scanning. It offers a comprehensive suite of features, including:
- Host Discovery: Identifying active hosts on a network, even those behind firewalls or other security measures.
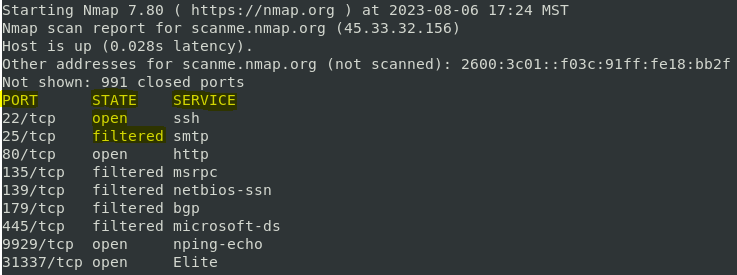
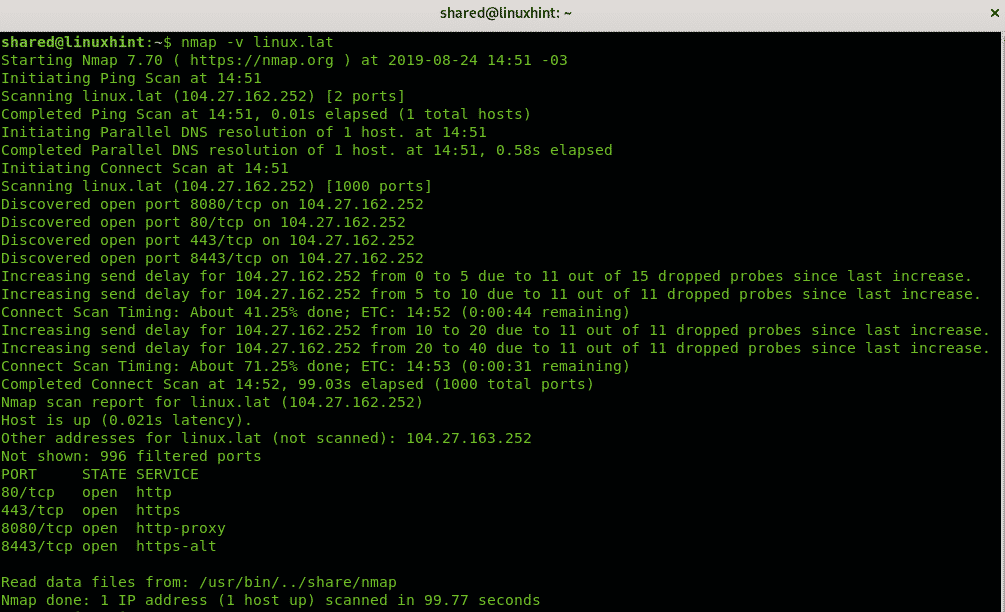
- Port Scanning: Determining which ports are open on a host and the services running on those ports.
- Operating System Detection: Identifying the operating system running on a target host based on network responses.
- Service Version Detection: Determining the specific versions of services running on open ports.
- Vulnerability Scanning: Identifying known vulnerabilities in target systems based on their operating system, services, and configurations.
- Network Mapping: Visualizing the network topology, including connections between hosts and devices.
- Script Scanning: Automating security checks and gathering additional information using custom scripts.
Nmap in Action: A Practical Demonstration
To illustrate the practical application of Nmap, consider the scenario of a network administrator tasked with identifying all active hosts on a corporate network. Using the basic command nmap -sn 192.168.1.0/24, Nmap would scan the specified IP range (192.168.1.0 to 192.168.1.255) and list all active hosts within that range.
Delving Deeper: Advanced Nmap Techniques
Nmap’s power lies in its ability to be tailored to specific needs. Advanced techniques allow for targeted scans, increased stealth, and enhanced data collection:
- Stealth Scanning: Using techniques like TCP SYN scan or FIN scan to minimize the scan’s footprint and reduce the likelihood of detection by intrusion detection systems (IDS).
- Target Specific Ports: Scanning only a specific range of ports, such as those commonly used for web services (ports 80 and 443).
- Custom Scripts: Leveraging Nmap’s extensive library of scripts for automating security checks, gathering specific information, or performing unique tasks.
- Timing and Rate Limiting: Controlling the scan’s speed and minimizing its impact on network performance.
- Output Customization: Generating scan results in various formats, including text, XML, and CSV, for easy analysis and reporting.
Beyond the Basics: Expanding Nmap’s Potential
Nmap’s versatility extends beyond basic scanning. It can be integrated with other tools and techniques to enhance security assessments and network management:
- Nmap with Nessus: Combining Nmap’s host discovery and port scanning with Nessus’s vulnerability scanning capabilities for comprehensive security assessments.
- Nmap with Metasploit: Utilizing Nmap’s scan results to identify potential targets for penetration testing and exploit development.
- Nmap with Wireshark: Correlating Nmap scan results with network traffic captured by Wireshark for deeper analysis and troubleshooting.
- Nmap for Network Troubleshooting: Utilizing Nmap’s traceroute and ping capabilities to identify network bottlenecks and connectivity issues.
Navigating the Landscape: FAQs on Nmap
Q: What are the key benefits of using Nmap?
A: Nmap offers numerous benefits, including:
- Comprehensive network visibility: Gaining a complete understanding of the network landscape, including active hosts, open ports, and running services.
- Enhanced security assessments: Identifying potential vulnerabilities and security risks in target systems.
- Network troubleshooting: Diagnosing connectivity issues and identifying network bottlenecks.
- Flexibility and customization: Tailoring scans to specific needs through advanced techniques and custom scripting.
Q: Is Nmap legal to use?
A: Nmap itself is a legitimate tool for network administration and security assessment. However, its use can raise ethical and legal concerns depending on the context. Using Nmap to scan networks without permission may be considered illegal in some jurisdictions.
Q: How can I learn more about Nmap?
A: Nmap’s official website (nmap.org) provides comprehensive documentation, tutorials, and resources for learning and mastering the tool.
Q: What are some best practices for using Nmap?
A: It’s crucial to use Nmap responsibly and ethically. Some best practices include:
- Obtain permission before scanning networks: Respecting the privacy and security of others.
- Limit the scope of scans: Focusing on specific targets and minimizing the impact on network performance.
- Use stealth scanning techniques: Reducing the scan’s footprint and avoiding detection by security systems.
- Regularly update Nmap: Ensuring access to the latest features and security patches.
Conclusion: The Indispensable Tool for Network Professionals
Nmap stands as an indispensable tool for network professionals, security researchers, and anyone seeking to gain deeper insights into network infrastructure. Its versatility, power, and open-source nature make it a valuable asset for network administration, security assessment, and troubleshooting. By mastering Nmap’s capabilities, individuals can unlock a world of network knowledge and enhance their ability to protect and manage networks effectively.





Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap. We hope you find this article informative and beneficial. See you in our next article!