Unlocking Network Insights with Nmap Python Scripts
Related Articles: Unlocking Network Insights with Nmap Python Scripts
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unlocking Network Insights with Nmap Python Scripts. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking Network Insights with Nmap Python Scripts
- 2 Introduction
- 3 Unlocking Network Insights with Nmap Python Scripts
- 3.1 Understanding Nmap Python Scripts: A Bridge Between Power and Flexibility
- 3.2 A Closer Look at Nmap Python Script Functionality: Diving into the Core Capabilities
- 3.3 Building Your First Nmap Python Script: A Practical Introduction
- 3.4 Unlocking the Power of Nmap Python Scripts: Real-World Applications
- 3.5 FAQs: Addressing Common Queries About Nmap Python Scripts
- 3.6 Tips for Effective Nmap Python Scripting: Optimizing Efficiency and Functionality
- 3.7 Conclusion: Embracing the Power of Nmap Python Scripts
- 4 Closure
Unlocking Network Insights with Nmap Python Scripts

Network scanning is an essential practice for network administrators, security professionals, and anyone seeking to understand the structure and behavior of a network. While the Nmap command-line tool provides a powerful set of features, leveraging its capabilities through Python scripting unlocks a new level of automation, customization, and integration.
This article delves into the world of Nmap Python scripts, exploring their functionality, benefits, and practical applications.
Understanding Nmap Python Scripts: A Bridge Between Power and Flexibility
Nmap Python scripts, often referred to as "NSE scripts," extend Nmap’s capabilities by allowing users to automate tasks, perform custom scans, and interact with network devices in a more sophisticated manner. These scripts leverage the Nmap Scripting Engine (NSE), a powerful framework that provides access to Nmap’s core functionality and a library of pre-built scripts for common tasks.
The fundamental concept behind Nmap Python scripts is to leverage the power of Python’s versatility and flexibility to interact with Nmap’s scanning capabilities. This allows for:
- Automated Scanning: Repetitive tasks, such as scanning a range of IP addresses or performing vulnerability checks, can be automated, saving time and effort.
- Customizable Scan Profiles: Scripts can be tailored to specific needs, allowing for the creation of unique scan profiles that target specific vulnerabilities or services.
- Data Extraction and Analysis: Scripts can extract data from scan results, analyze it, and present it in a user-friendly format, enabling deeper insights into network behavior.
- Integration with Other Tools: Scripts can be integrated with other tools and systems, such as logging frameworks, databases, or security information and event management (SIEM) platforms.
A Closer Look at Nmap Python Script Functionality: Diving into the Core Capabilities
Nmap Python scripts are built using the Nmap Scripting Engine (NSE), a powerful framework that provides a range of functions and objects for interacting with Nmap’s core functionality. Here are some key aspects of NSE functionality:
- Network Interaction: Scripts can send and receive network packets, allowing for direct interaction with network devices.
- Port Scanning: Scripts can access Nmap’s port scanning capabilities, identifying open ports and associated services.
- Service Detection: Scripts can utilize Nmap’s service detection mechanisms to identify specific services running on discovered ports.
- Data Parsing: Scripts can parse data from Nmap scans, including host information, port details, and service fingerprints.
- Output Generation: Scripts can generate custom output formats, such as text files, HTML reports, or database entries.
- External Libraries: Scripts can leverage external Python libraries to enhance functionality, including libraries for data analysis, visualization, and security auditing.
Building Your First Nmap Python Script: A Practical Introduction
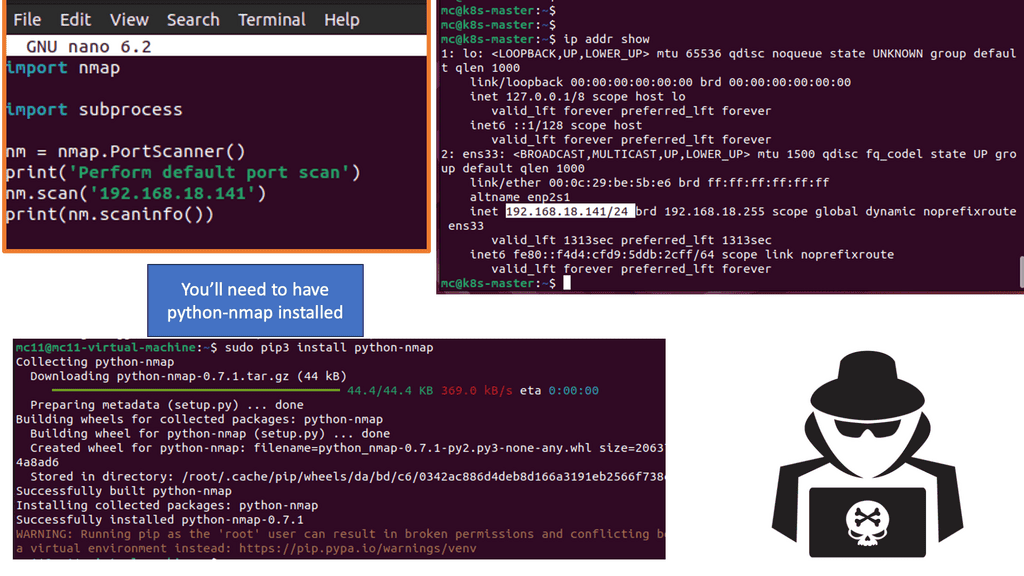
Creating a basic Nmap Python script involves understanding the fundamental structure and syntax. While numerous examples and templates exist, let’s explore a simple script that performs a basic port scan and prints the results:
import nmap
# Create a Nmap scanner object
scanner = nmap.PortScanner()
# Define the target IP address
target_ip = "192.168.1.1"
# Perform a port scan for ports 22 and 80
scanner.scan(hosts=target_ip, arguments="-p 22,80")
# Print the scan results
print(scanner.all_hosts())
# Print the details of each open port
for host in scanner.all_hosts():
for proto in scanner[host].all_protocols():
print('----------')
print('Host: %s (%s)' % (host, scanner[host]['addresses']['ipv4']))
print('Protocol: %s' % proto)
lport = scanner[host][proto].keys()
for port in lport:
print('port: %ststate: %s' % (port, scanner[host][proto][port]['state']))This script demonstrates the basic steps involved in creating a Nmap Python script:
-
Import the
nmaplibrary: This line imports the necessary library for interacting with Nmap. -
Create a scanner object: This line creates an instance of the
PortScannerclass, representing the Nmap scanner. - Define the target IP: This line specifies the IP address to scan.
-
Perform the scan: This line executes the scan using the
scan()method, specifying the target IP and desired ports. - Print the results: This section prints the scan results, including host information and open ports.
This example provides a simple illustration of the fundamental concepts involved in Nmap Python scripting.
Unlocking the Power of Nmap Python Scripts: Real-World Applications
Nmap Python scripts offer a wide range of practical applications across various domains, including network administration, security auditing, and penetration testing. Here are some examples:
- Network Discovery and Inventory: Scripts can automatically scan networks to identify active devices, gather information about their operating systems and services, and create network maps.
- Vulnerability Scanning: Scripts can be used to identify vulnerabilities in systems and applications by performing targeted scans and analyzing scan results.
- Service Auditing: Scripts can automate the process of auditing network services, checking for misconfigurations and potential security risks.
- Firewall Rule Management: Scripts can be used to automate the creation and management of firewall rules based on network discovery and security assessments.
- Network Monitoring: Scripts can be integrated with monitoring tools to provide real-time insights into network activity and alert on suspicious behavior.
- Penetration Testing: Scripts can be used to simulate attacks and identify potential vulnerabilities in systems and applications.
FAQs: Addressing Common Queries About Nmap Python Scripts
1. What are the prerequisites for using Nmap Python scripts?
To use Nmap Python scripts, you need:
- Nmap installed: The Nmap command-line tool must be installed on your system.
- Python installed: Python must be installed on your system.
-
Nmap Python library: The
nmapPython library must be installed. This can typically be done usingpip install python-nmap.
2. How can I find existing Nmap Python scripts?
Nmap’s official website provides a comprehensive library of pre-built scripts, covering a wide range of tasks. Additionally, online repositories like GitHub host numerous community-developed scripts.
3. How do I debug Nmap Python scripts?
Debugging Nmap Python scripts is similar to debugging any Python code. You can utilize standard debugging techniques such as print statements, logging, and using a debugger.
4. Can I integrate Nmap Python scripts with other tools?
Yes, Nmap Python scripts can be integrated with other tools and systems through various mechanisms. For example, you can use libraries like requests to interact with APIs, pandas for data analysis, and matplotlib for visualization.
5. What are the security implications of using Nmap Python scripts?
While Nmap itself is a powerful tool for network discovery and security auditing, it is important to use it responsibly and ethically. Ensure that you have the necessary permissions and understanding of legal and ethical implications before using Nmap Python scripts.
Tips for Effective Nmap Python Scripting: Optimizing Efficiency and Functionality
-
Use the
nmaplibrary: ThenmapPython library provides a comprehensive interface for interacting with Nmap’s core functionality. - Leverage pre-built scripts: Nmap’s official website and online repositories offer a wealth of pre-built scripts that can be adapted to your needs.
- Write modular scripts: Break down complex tasks into smaller, reusable modules to improve code organization and maintainability.
- Use comments and documentation: Document your scripts clearly to enhance readability and understanding.
- Test your scripts thoroughly: Test your scripts on a controlled network environment to ensure they work as expected.
- Use error handling: Implement error handling mechanisms to catch unexpected errors and prevent script crashes.
- Consider security implications: Always be aware of the potential security implications of using Nmap Python scripts.
Conclusion: Embracing the Power of Nmap Python Scripts
Nmap Python scripts offer a powerful and flexible approach to network exploration and analysis. By combining Nmap’s core capabilities with Python’s versatility, these scripts unlock a new level of automation, customization, and integration, enabling users to gain deeper insights into network behavior and security posture.
Whether you’re a network administrator seeking to streamline routine tasks, a security professional conducting vulnerability assessments, or a penetration tester simulating attacks, Nmap Python scripts provide a valuable tool for leveraging the power of network scanning.





Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Insights with Nmap Python Scripts. We hope you find this article informative and beneficial. See you in our next article!