Nmap: A Powerful Toolkit for Network Exploration and Security Auditing
Related Articles: Nmap: A Powerful Toolkit for Network Exploration and Security Auditing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap: A Powerful Toolkit for Network Exploration and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: A Powerful Toolkit for Network Exploration and Security Auditing

Nmap, short for Network Mapper, is a powerful open-source tool used for network discovery and security auditing. Developed by Gordon Lyon (also known as Fyodor), Nmap has become an indispensable tool for network administrators, security professionals, and researchers worldwide. Its versatility and comprehensive feature set allow users to perform a wide range of network tasks, from simple host discovery to intricate vulnerability scanning.
Understanding the Core Functionality of Nmap
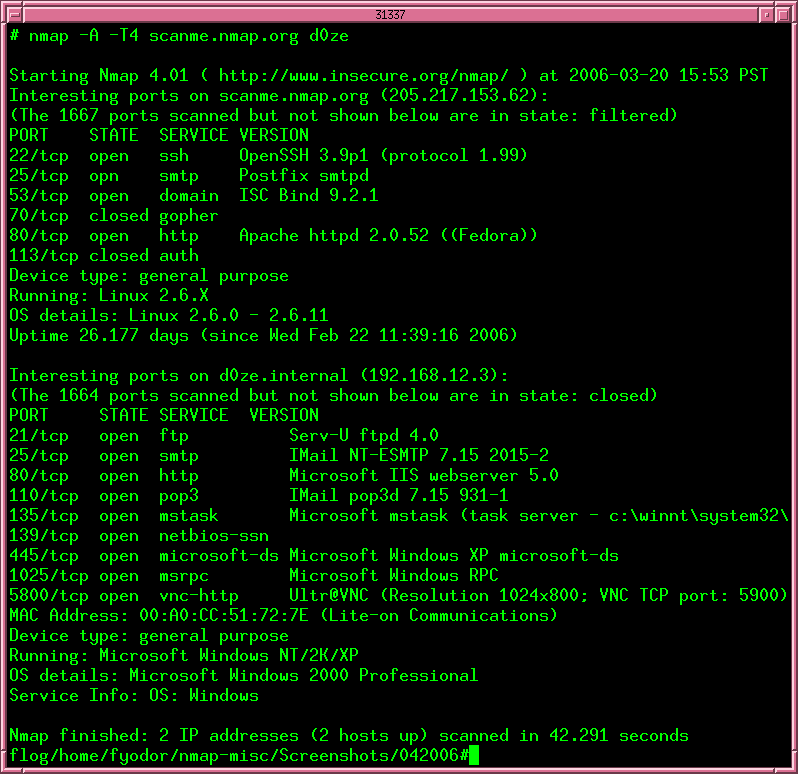
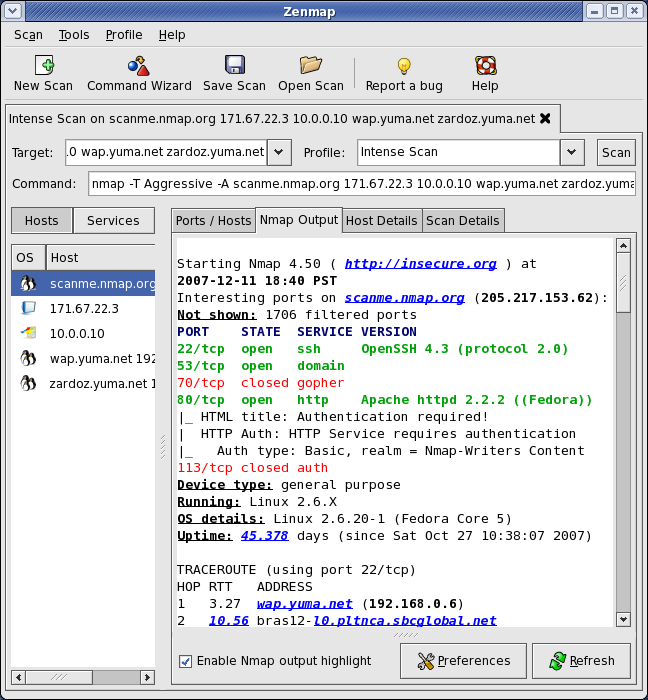
At its core, Nmap operates by sending specially crafted packets to target networks or devices and analyzing the responses. These packets can be tailored to elicit specific information about the target, such as its operating system, open ports, and running services. This information is then presented to the user in a clear and organized format, enabling them to gain a comprehensive understanding of the network’s structure and security posture.
Exploring the Capabilities of Nmap
Nmap’s capabilities extend far beyond basic host discovery. It offers a wide array of features, including:
- Host Discovery: Identifying active hosts on a network, including their IP addresses, MAC addresses, and operating systems.
- Port Scanning: Determining which ports are open on a target host and the services running on those ports.
- Operating System Detection: Identifying the operating system of target devices based on their network responses.
- Service Version Detection: Determining the versions of services running on open ports, allowing for potential vulnerability identification.
- Vulnerability Scanning: Identifying known vulnerabilities in target systems and applications.
- Network Mapping: Creating visual representations of network topologies, highlighting connections between devices.
- Script Scanning: Executing custom scripts to perform specialized tasks, such as banner grabbing or detecting specific vulnerabilities.
Nmap in Action: Real-World Applications
Nmap’s versatility makes it applicable across a wide range of scenarios:
- Network Administration: Network administrators use Nmap for tasks such as network discovery, host inventory, and troubleshooting connectivity issues.
- Security Auditing: Security professionals utilize Nmap to identify vulnerabilities, assess security posture, and detect potential threats.
- Penetration Testing: Penetration testers employ Nmap to discover attack surfaces, identify potential entry points, and validate the effectiveness of security measures.
- Research and Development: Researchers and developers use Nmap to analyze network traffic, study network protocols, and explore new security concepts.
- Incident Response: Incident responders leverage Nmap to gather information about compromised systems, identify attackers, and contain the spread of malware.
Nmap’s Impact on the Security Landscape
Nmap has played a crucial role in shaping the security landscape by:
- Empowering Security Professionals: Nmap provides security professionals with a powerful tool for identifying and mitigating vulnerabilities, enhancing overall security posture.
- Promoting Transparency: Nmap’s open-source nature fosters transparency and allows for community collaboration in improving security practices.
- Driving Vulnerability Research: Nmap’s versatility and scripting capabilities encourage researchers to develop new techniques for identifying vulnerabilities, leading to continuous improvements in security.
FAQs about Nmap Projects
1. Is Nmap legal to use?
Nmap is legal to use for ethical purposes such as network administration, security auditing, and research. However, using Nmap for malicious activities like unauthorized access or denial-of-service attacks is illegal and unethical.
2. How can I learn to use Nmap effectively?
Nmap offers comprehensive documentation, tutorials, and online resources to assist users in learning its functionality. The official Nmap website, Nmap.org, provides an extensive knowledge base and guides for both beginners and advanced users.
3. Are there any alternatives to Nmap?
While Nmap is widely considered the gold standard for network scanning, other tools offer similar functionalities, such as:
- Advanced Port Scanner (Acunetix)
- Nessus
- OpenVAS
- Zenmap (Nmap’s graphical interface)
4. How can I protect my network from Nmap scans?
While completely preventing Nmap scans is challenging, organizations can implement security measures to mitigate their impact, such as:
- Firewall Configuration: Configure firewalls to block unauthorized traffic and restrict access to sensitive ports.
- Intrusion Detection Systems (IDS): Deploy IDS to monitor network traffic for suspicious activity and alert administrators to potential attacks.
- Network Segmentation: Divide the network into smaller segments to limit the scope of potential attacks and restrict access to sensitive data.
- Security Awareness Training: Educate employees about the risks of network scanning and encourage them to report any suspicious activity.
Tips for Effective Nmap Utilization
- Start with Basic Scans: Begin with simple scans to gather initial information about the target network before moving on to more complex scans.
- Use Nmap’s Scripting Capabilities: Leverage Nmap’s scripting capabilities to automate tasks and perform specialized scans.
- Understand Nmap Output: Familiarize yourself with Nmap’s output format and learn to interpret the results effectively.
- Combine Nmap with Other Tools: Integrate Nmap with other security tools for a more comprehensive security assessment.
- Stay Updated: Keep your Nmap installation and scripts up-to-date to benefit from the latest features and security enhancements.
Conclusion
Nmap remains a powerful and versatile tool for network exploration and security auditing. Its extensive feature set, comprehensive documentation, and active community support have made it an indispensable resource for network administrators, security professionals, and researchers worldwide. As the security landscape continues to evolve, Nmap’s capabilities will continue to adapt and play a crucial role in safeguarding networks and protecting sensitive information. By understanding Nmap’s functionality, utilizing its features effectively, and staying informed about its latest developments, users can leverage its power to enhance network security and mitigate potential threats.






Closure
Thus, we hope this article has provided valuable insights into Nmap: A Powerful Toolkit for Network Exploration and Security Auditing. We appreciate your attention to our article. See you in our next article!