Navigating the Network Landscape: A Comprehensive Guide to Nmap’s Python Documentation
Related Articles: Navigating the Network Landscape: A Comprehensive Guide to Nmap’s Python Documentation
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating the Network Landscape: A Comprehensive Guide to Nmap’s Python Documentation. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Network Landscape: A Comprehensive Guide to Nmap’s Python Documentation

Nmap, the Network Mapper, is a powerful and versatile tool for network exploration and security auditing. Its ability to scan networks, identify open ports, and gather information about hosts makes it an indispensable resource for network administrators, security professionals, and researchers. While Nmap’s command-line interface provides a robust and efficient method for conducting scans, its Python library offers a more programmatic and flexible approach. This article delves into the intricacies of Nmap’s Python documentation, offering a comprehensive guide for those seeking to harness the power of Nmap through Python scripting.
Understanding the Foundation: Nmap’s Python Library
Nmap’s Python library, aptly named nmap, provides a Pythonic interface to the core functionality of Nmap, allowing users to leverage its capabilities within their Python scripts. This library offers a streamlined way to perform network scans, analyze results, and integrate Nmap’s features into larger automation workflows. The documentation serves as the vital bridge between the user and the library, providing a roadmap for navigating its functionalities and understanding its nuances.
Unveiling the Documentation: Structure and Content
Nmap’s Python documentation is meticulously structured, offering a clear and logical path for users to access the information they need. It follows a consistent format, starting with a concise overview of the library’s capabilities and then diving into the core functions, classes, and methods. Each section is accompanied by detailed explanations, illustrative examples, and practical usage scenarios.
Delving Deeper: Key Documentation Components
-
Introduction: This section lays the groundwork, providing a high-level overview of the Nmap Python library. It highlights the library’s purpose, its relationship to the Nmap command-line tool, and its key benefits.
-
Installation and Setup: A crucial step for any library, the documentation provides clear instructions on installing and configuring the Nmap Python library. It covers various installation methods, including using pip, the Python package manager.
-
Core Functionality: This section forms the heart of the documentation, outlining the library’s primary functions and classes. It delves into the specifics of performing scans, analyzing results, and manipulating data.
-
Scanning: The documentation provides comprehensive guidance on conducting various types of scans, including:
- Host Discovery: Identifying active hosts on a network.
- Port Scanning: Determining open ports on target hosts.
- Service Detection: Identifying running services on open ports.
- Operating System Detection: Identifying the operating systems of target hosts.
- Version Detection: Determining the versions of services running on target hosts.
-
Result Analysis: The documentation explains how to extract and analyze scan results, including:
- Accessing Scan Data: Retrieving information about scanned hosts, ports, and services.
- Data Manipulation: Processing and transforming scan results for further analysis or visualization.
- Result Interpretation: Understanding the meaning of scan results and drawing meaningful conclusions.
-
Scanning: The documentation provides comprehensive guidance on conducting various types of scans, including:
-
Advanced Features: Nmap’s Python library offers a range of advanced features, which the documentation covers in detail. These features include:
- Custom Scan Scripts: The documentation explains how to write custom scan scripts using the Nmap Scripting Engine (NSE), allowing users to tailor scans to their specific needs.
- Network Mapping: The documentation guides users on creating network maps based on scan results, providing a visual representation of network topology.
- Integration with Other Tools: The documentation outlines how to integrate the Nmap Python library with other tools and frameworks, such as security information and event management (SIEM) systems.
-
Examples and Tutorials: Nmap’s Python documentation provides a wealth of practical examples and tutorials, demonstrating how to utilize the library in real-world scenarios. These examples range from simple scan scripts to complex network analysis workflows, offering a hands-on learning experience.
Frequently Asked Questions (FAQs)
-
Q: What are the prerequisites for using Nmap’s Python library?
- A: The primary prerequisite is a Python installation. The library is compatible with Python 2.7 and later versions. It’s also recommended to have the Nmap command-line tool installed, as the Python library relies on it for certain functionalities.
-
Q: How do I access the documentation?
- A: Nmap’s Python documentation is readily available online at https://nmap.org/book/nmap-python-api.html. It’s also included in the Nmap source code distribution.
-
Q: Can I use the library for both basic and advanced network scans?
- A: Yes, the library supports both basic and advanced scan types, providing flexibility for users with varying levels of expertise. It allows for simple host discovery scans as well as complex, customized scans tailored to specific security auditing needs.
-
Q: Can I integrate the library into my existing Python projects?
- A: Absolutely. The library is designed to integrate seamlessly with other Python libraries and frameworks. It can be incorporated into various projects, such as network monitoring systems, security automation scripts, and research projects.
-
Q: Is there a community for support and assistance?
- A: Yes, Nmap has a vibrant community of users and developers. The Nmap mailing list and forums are excellent resources for seeking help, sharing knowledge, and engaging in discussions.
Tips for Effective Use
- Start with the Basics: Begin by exploring the introductory documentation and the core functionality section to familiarize yourself with the library’s fundamental concepts and features.
- Experiment with Examples: Utilize the provided examples and tutorials to gain hands-on experience and understand how to implement the library in practical scenarios.
- Consult the Reference Manual: Refer to the reference manual for detailed information on specific functions, classes, and methods.
- Leverage the Community: Engage with the Nmap community for support, guidance, and knowledge sharing.
Conclusion
Nmap’s Python documentation serves as an invaluable resource for anyone seeking to harness the power of Nmap within Python scripts. Its comprehensive structure, detailed explanations, and practical examples empower users to navigate the complexities of network security and analysis with ease. By understanding the library’s functionalities and leveraging the documentation’s guidance, users can unlock a world of possibilities, integrating Nmap’s capabilities into their own projects and workflows. Whether conducting basic network scans, performing advanced security audits, or developing custom network analysis tools, Nmap’s Python library and its accompanying documentation provide a solid foundation for achieving success.

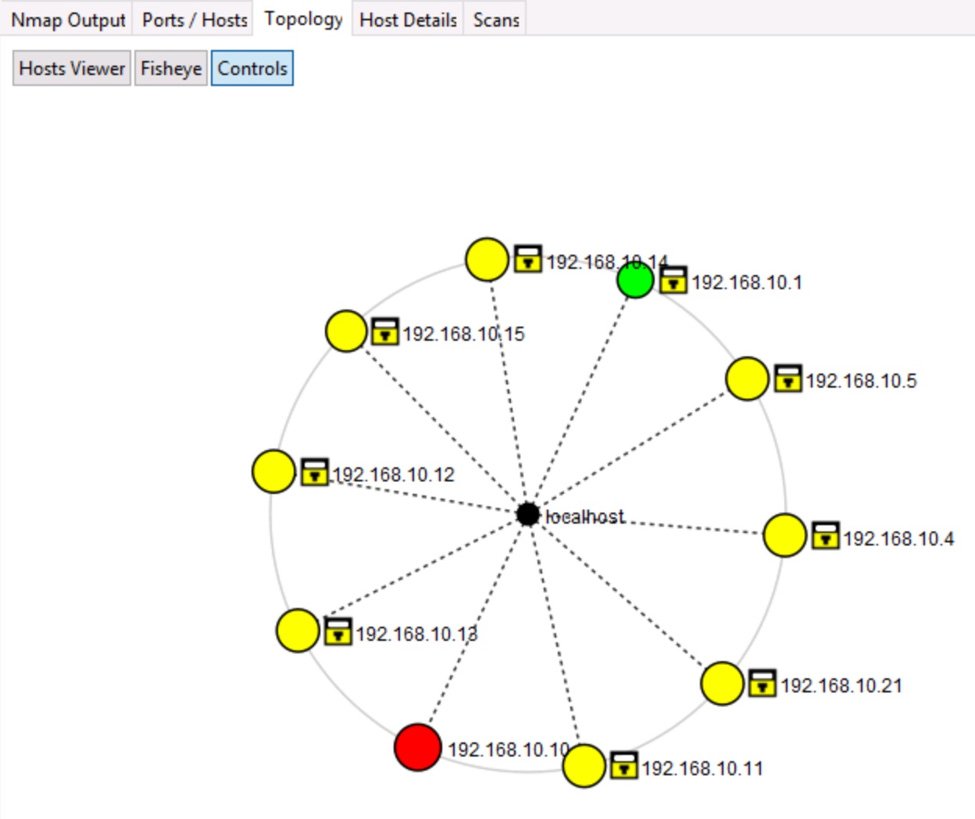


Closure
Thus, we hope this article has provided valuable insights into Navigating the Network Landscape: A Comprehensive Guide to Nmap’s Python Documentation. We hope you find this article informative and beneficial. See you in our next article!