Navigating the Complexities of IMAP Policy: A Comprehensive Guide
Related Articles: Navigating the Complexities of IMAP Policy: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Complexities of IMAP Policy: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Complexities of IMAP Policy: A Comprehensive Guide

The world of email is a complex ecosystem, governed by a set of protocols that ensure smooth communication. Among these, the Internet Message Access Protocol (IMAP) plays a crucial role, enabling users to access and manage their emails from multiple devices. However, the effectiveness of IMAP relies heavily on the implementation of a robust and well-defined policy. This policy governs how IMAP is used within an organization, ensuring security, efficiency, and compliance with relevant regulations.
Understanding the Core of IMAP Policy
IMAP policy, at its core, aims to establish a framework for managing email access and usage within a specific environment. It encompasses various aspects, including:
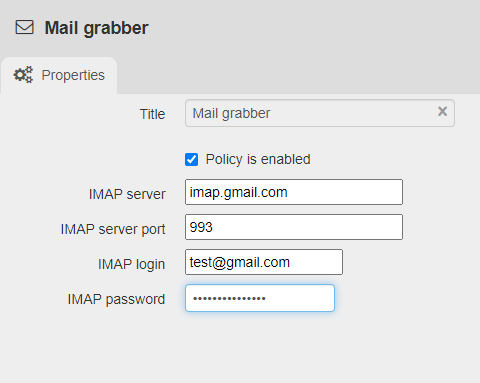
- Authentication and Authorization: Defining stringent authentication mechanisms to verify user identities and grant access to specific email accounts. This helps prevent unauthorized access and data breaches.
- Access Control: Establishing clear rules about who can access what data within the email system. This could include restricting access to specific folders, limiting the number of devices that can access an account, or setting time-based restrictions.
- Data Retention and Archiving: Implementing policies for email storage, retention, and archiving. This ensures compliance with legal and regulatory requirements while also facilitating efficient data management.
- Security Measures: Implementing security protocols to protect email data from unauthorized access, malware, and other threats. This might include encryption, spam filtering, and anti-virus measures.
- Compliance with Regulations: Ensuring that email usage practices align with relevant legal and regulatory frameworks, such as GDPR, HIPAA, or SOX.
The Importance of a Comprehensive IMAP Policy
A well-defined IMAP policy is vital for any organization that relies heavily on email communication. Its benefits extend across various aspects:
- Security Enhancement: A robust IMAP policy significantly strengthens email security by implementing authentication, access control, and encryption measures. This minimizes the risk of unauthorized access, data breaches, and malware infections.
- Improved Data Management: By establishing clear rules for email storage, retention, and archiving, IMAP policy facilitates efficient data management. This ensures that relevant information is readily available while also minimizing storage costs and eliminating unnecessary data clutter.
- Compliance with Regulations: A well-structured IMAP policy ensures adherence to relevant legal and regulatory frameworks, mitigating the risk of penalties and legal repercussions. This is particularly crucial for organizations handling sensitive personal data.
- Enhanced Productivity: By streamlining email access and management, IMAP policy can significantly enhance user productivity. This includes minimizing downtime, facilitating seamless collaboration, and ensuring that users have access to the information they need when they need it.
- Cost Reduction: By optimizing email storage and minimizing security risks, IMAP policy can contribute to cost reduction. This includes reducing storage costs, minimizing the impact of data breaches, and streamlining administrative overhead.
FAQs Regarding IMAP Policy
1. What are the key elements of a comprehensive IMAP policy?
A comprehensive IMAP policy should address the following key elements:
- Authentication and Authorization: Clear procedures for verifying user identities and granting access to email accounts.
- Access Control: Specific rules defining who can access which email data, including folder permissions and device restrictions.
- Data Retention and Archiving: Policies for storing, retaining, and archiving email data, including retention periods and data backup procedures.
- Security Measures: Implementation of security protocols, such as encryption, spam filtering, and anti-virus measures, to protect email data from threats.
- Compliance with Regulations: Alignment with relevant legal and regulatory frameworks, including GDPR, HIPAA, or SOX.
2. How can an organization enforce its IMAP policy?
Enforcing an IMAP policy involves a combination of technical and administrative measures:
- Technical Measures: Implementing access control mechanisms, encryption protocols, and spam filters to enforce policy restrictions.
- Administrative Measures: Communicating the policy clearly to users, providing training on best practices, and monitoring compliance through audits and log analysis.
3. What are the potential consequences of not having a proper IMAP policy?
Failing to implement a robust IMAP policy can lead to various negative consequences:
- Security Breaches: Increased risk of unauthorized access, data breaches, and malware infections.
- Compliance Violations: Legal and regulatory penalties for non-compliance with data protection laws.
- Productivity Loss: Disruption of email access and communication, leading to productivity loss and operational inefficiencies.
- Reputation Damage: Negative publicity and reputational damage due to data breaches or compliance violations.
Tips for Implementing a Successful IMAP Policy
1. Involve Stakeholders: Engage relevant stakeholders, including IT personnel, legal teams, and end-users, in the policy development process. This ensures that the policy is practical, comprehensive, and addresses the needs of all parties involved.
2. Clarity and Conciseness: Ensure that the policy is written clearly and concisely, using simple language that is easily understandable by all users.
3. Regular Review and Updates: Periodically review and update the policy to reflect changes in technology, regulations, and organizational needs. This ensures that the policy remains relevant and effective.
4. Training and Communication: Provide comprehensive training to users on the policy’s requirements and best practices for email usage. This fosters understanding and promotes compliance.
5. Monitoring and Enforcement: Implement robust monitoring mechanisms to track compliance with the policy and enforce its provisions effectively. This includes regular audits, log analysis, and incident response procedures.
Conclusion
A well-defined and effectively implemented IMAP policy is essential for any organization that relies on email communication. It safeguards sensitive data, ensures regulatory compliance, enhances productivity, and minimizes the risk of security breaches. By carefully considering the key elements, engaging stakeholders, and adhering to best practices, organizations can establish a robust IMAP policy that fosters a secure, efficient, and compliant email environment.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Complexities of IMAP Policy: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!
