Navigating Network Landscapes: A Comprehensive Guide to the Nmap Python Module
Related Articles: Navigating Network Landscapes: A Comprehensive Guide to the Nmap Python Module
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating Network Landscapes: A Comprehensive Guide to the Nmap Python Module. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating Network Landscapes: A Comprehensive Guide to the Nmap Python Module

The Nmap (Network Mapper) tool, renowned for its network scanning capabilities, has gained immense popularity in the cybersecurity community. Its versatility extends beyond command-line execution, thanks to the robust Nmap Python module, providing developers with a powerful interface to integrate Nmap’s functionality within their scripts and applications. This article delves into the intricacies of the Nmap Python module, exploring its features, benefits, and practical applications.
Understanding the Nmap Python Module
The Nmap Python module acts as a bridge between the core Nmap functionality and Python scripts, enabling seamless interaction with the network scanning tool. It provides a high-level interface to Nmap’s diverse capabilities, simplifying the process of launching scans, interpreting results, and manipulating data. This Python module empowers developers to:
- Execute Nmap Scans: Launch various Nmap scans, including port scans, OS detection, service version identification, and vulnerability checks, directly from Python code.
- Customize Scan Parameters: Fine-tune scan parameters like target hosts, ports, scan types, and timing settings to tailor scans to specific requirements.
- Parse Scan Results: Extract and analyze scan data, including host information, open ports, services, and operating systems, using Python’s data structures and analysis tools.
- Integrate with Other Tools and Libraries: Combine Nmap’s network insights with other Python libraries and tools for data processing, visualization, and security automation.
Benefits of Using the Nmap Python Module
The Nmap Python module offers a plethora of benefits for developers and security professionals:
- Enhanced Scripting Capabilities: The module enables developers to incorporate Nmap’s network scanning capabilities within their Python scripts, automating network analysis and security tasks.
- Improved Efficiency and Automation: By integrating Nmap into Python workflows, developers can streamline network scanning processes, reducing manual effort and enhancing efficiency.
- Increased Flexibility and Control: The Python interface grants greater control over scan parameters, allowing for customized network analysis based on specific requirements.
- Data Integration and Analysis: The module facilitates the extraction and manipulation of Nmap scan data within Python environments, enabling comprehensive analysis and insights.
- Cross-Platform Compatibility: The Nmap Python module is compatible with various operating systems, ensuring seamless integration across different development environments.
A Practical Guide to Using the Nmap Python Module
This section provides a step-by-step guide to utilizing the Nmap Python module, illustrating its key functionalities through practical examples.
Installation and Setup:
- Install Nmap: Ensure Nmap is installed on your system. Refer to the Nmap documentation for installation instructions.
-
Install the Nmap Python Module: Use the following command to install the Nmap Python module:
pip install python-nmap
Basic Scan Example:
import nmap
scanner = nmap.PortScanner()
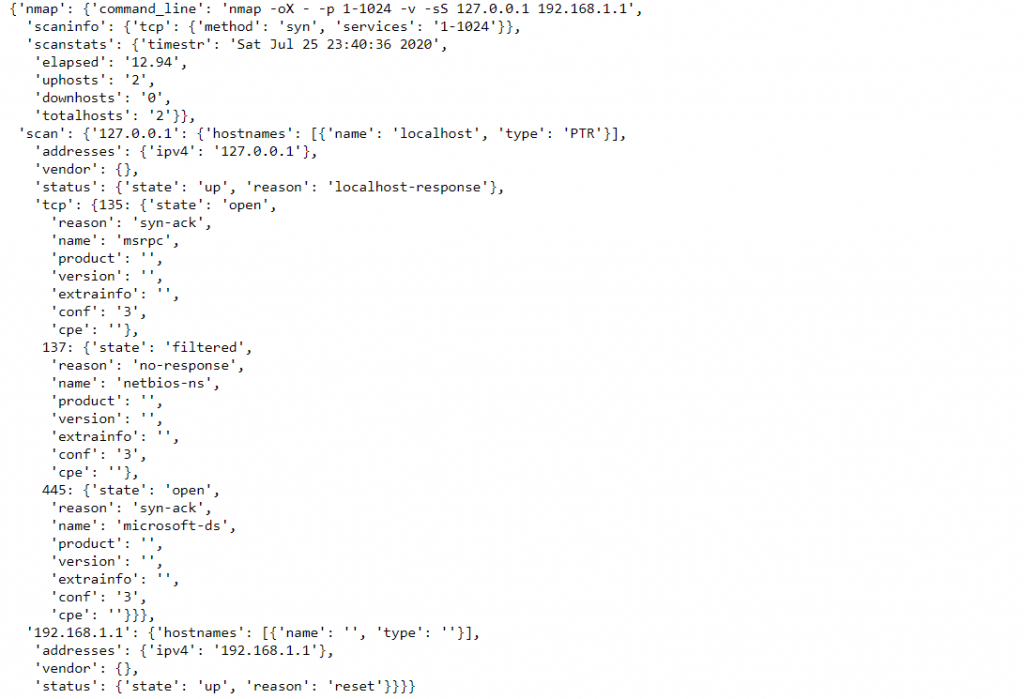
scanner.scan(hosts='192.168.1.1', arguments='-T4 -F')
for host in scanner.all_hosts():
print('--------------------------------------------------')
print('Host : %s (%s)' % (host, scanner[host]['status']['state']))
print('State : %s' % scanner[host]['status']['state'])
for proto in scanner[host].all_protocols():
print('----------')
print('Protocol : %s' % proto)
lport = scanner[host][proto].keys()
for port in lport:
print('port : %ststate : %s' % (port, scanner[host][proto][port]['state']))This example demonstrates a basic port scan targeting the IP address 192.168.1.1. The -T4 argument specifies a fast scan, while -F limits the scan to common ports. The code then iterates through the scan results, printing host information, protocols, and port states.
Advanced Scan Options:
The Nmap Python module supports a wide range of advanced scan options, including:
- OS Detection: Identify the operating system running on target hosts.
- Service Version Identification: Determine the versions of services running on open ports.
- Vulnerability Scanning: Detect known vulnerabilities in target systems.
- Custom Scan Scripts: Execute custom Nmap scripts to perform specific tasks.
Example: OS Detection and Service Version Identification
import nmap
scanner = nmap.PortScanner()
scanner.scan(hosts='192.168.1.1', arguments='-T4 -sV -O')
for host in scanner.all_hosts():
print('--------------------------------------------------')
print('Host : %s (%s)' % (host, scanner[host]['status']['state']))
print('State : %s' % scanner[host]['status']['state'])
if 'osmatch' in scanner[host]:
print('OS : %s' % scanner[host]['osmatch'][0]['name'])
for proto in scanner[host].all_protocols():
print('----------')
print('Protocol : %s' % proto)
lport = scanner[host][proto].keys()
for port in lport:
print('port : %ststate : %s' % (port, scanner[host][proto][port]['state']))
if 'name' in scanner[host][proto][port]:
print('service : %s' % scanner[host][proto][port]['name'])This example demonstrates the use of -sV (service version detection) and -O (OS detection) arguments to identify the operating system and service versions running on the target host. The code then prints the extracted information alongside the basic scan results.
Integrating with Other Tools and Libraries:
The Nmap Python module can be seamlessly integrated with other Python libraries and tools, expanding its capabilities and enabling sophisticated network analysis workflows. For instance:
- Data Visualization: Use libraries like Matplotlib or Seaborn to visualize Nmap scan data, creating insightful charts and graphs.
- Network Traffic Analysis: Combine Nmap scans with network analysis tools like Scapy or Wireshark to gain a comprehensive understanding of network activity.
- Security Automation: Integrate Nmap with security automation frameworks like Ansible or SaltStack to automate network security tasks.
FAQs about the Nmap Python Module
1. What is the difference between the Nmap Python module and the Nmap command-line tool?
The Nmap Python module provides a programmatic interface to Nmap’s functionality, allowing developers to integrate Nmap scans within their Python scripts. The Nmap command-line tool offers a more interactive and user-friendly interface for executing scans directly from the terminal.
2. Can I use the Nmap Python module for advanced scan options like vulnerability scanning?
Yes, the Nmap Python module supports advanced scan options, including vulnerability scanning. You can utilize Nmap’s vulnerability scanning scripts or integrate with external vulnerability scanning tools within your Python scripts.
3. How do I handle large-scale network scans using the Nmap Python module?
For large-scale network scans, consider using Nmap’s parallel scanning capabilities or leveraging distributed scanning tools like Nmap NSE (Nmap Scripting Engine). The Nmap Python module can be integrated with these tools to manage and analyze the results effectively.
4. Are there any limitations to using the Nmap Python module?
The Nmap Python module generally provides a comprehensive interface to Nmap’s features. However, some advanced functionalities might require direct interaction with the Nmap command-line tool or Nmap NSE scripts.
Tips for Effective Nmap Python Module Usage:
- Understand Nmap’s Command-Line Options: Familiarize yourself with Nmap’s command-line options to effectively utilize the module’s capabilities.
- Optimize Scan Parameters: Adjust scan parameters like timing, intensity, and port ranges to suit your specific requirements and minimize scan time.
- Handle Scan Results Efficiently: Use Python’s data structures and analysis tools to process and interpret scan results effectively.
- Integrate with Other Tools: Leverage the module’s integration capabilities to enhance network analysis and security automation workflows.
- Stay Updated: Regularly update the Nmap Python module and Nmap itself to benefit from the latest features and security improvements.
Conclusion
The Nmap Python module empowers developers and security professionals with a powerful tool to integrate Nmap’s network scanning capabilities into their Python scripts and applications. Its versatility, efficiency, and integration capabilities enable developers to automate network analysis tasks, extract valuable insights, and enhance security workflows. By leveraging the Nmap Python module, developers can unlock the full potential of Nmap, navigating the complex network landscape with ease and precision.

Closure
Thus, we hope this article has provided valuable insights into Navigating Network Landscapes: A Comprehensive Guide to the Nmap Python Module. We hope you find this article informative and beneficial. See you in our next article!